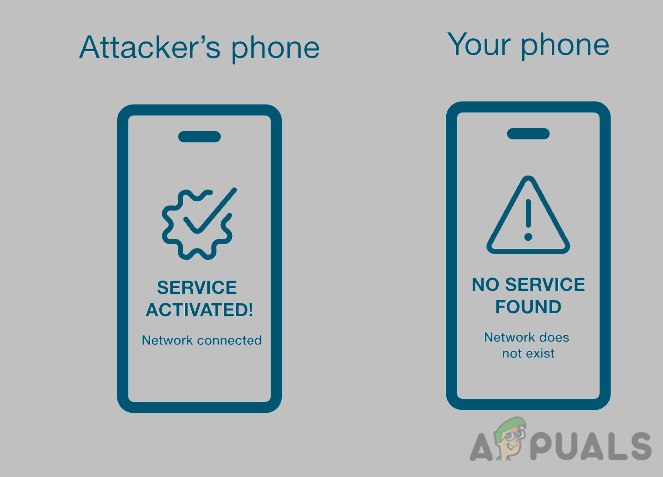
This 2FA technique is based on a consumer’s phone number, and the consumer must enter the code or OTP sent to his phone number to log into the required account/service. As technology is evolving, so do the scammers. One of the techniques they developed is a SIM swap attack called SIM swap scam, port-out scam, SIM jacking, SIM hijacking, SIM Intercept attack, etc.
Introduction of a SIM Swap Frauds/Attack
The telecom and I.T industries use your SIM to authenticate different actions like password reset on a website (although mobile numbers were not intended for this use). Due to this factor, your SIM is the magic key to many (if not all) essential services. Your bank accounts, email accounts, social media, and even online wallets (including crypto wallets) are tied to your phone number. Even the 2FA technique was developed to use your SIM to authorize a login to an account or service by entering a code sent to you either via call or text message to safeguard you even if your credentials were stolen. But the strength of this technique is also part of its weakness, as whoever possesses the phone or phone number will get the code. Hence, scammers developed the SIM swapping attack. A scammer may not be a hacker or tech-savvy with million-dollar equipment, he just needs a phone and a SIM card to perform his ill action. In this attack, scammers get a consumer’s phone number on their SIM (physical or E-SIM) by convincing the consumer’s carrier that they are the actual consumer and thus bypass the 2FA, opening hells of opportunities for them. This can be the worst of nightmares an individual may face as his SIM is virtually stolen but physically present with the consumer. In other words, a SIM swap attack occurs when a fraudster takes control of the victim’s phone number. The popularity of cryptocurrencies also increased the frequency of SIM swap attacks as the funds transferred from the victim’s crypto wallet are difficult to trace. Also, there are reports of data breaches on cryptocurrency exchanges, putting the data (especially the phone numbers of crypto owners) on sale on the black market. In 2020, Interpol arrested 10 fraudsters who were able to steal more than 100 million USD in cryptocurrencies by using SIM swap attacks. SIM swap attack is part social engineering as the fraudsters must know the personal details of the victim and part telecommunication fraud as the fraudsters must convince (or bribe) the telecom rep to issue the new SIM with the victim’s phone number. The most basic purpose of a SIM swap attack is to circumvent accounts’ security features based on messages or calls. SIM swapping attacks made the news headlines in 2017, although they were happening even before that. In the UK only, there is a reported surge in SIM swap attacks of 400% from 2015 to 2020. SIM swapping is a legitimate process if done by the original person but will be illegal if done by an imposter. SIM swapping is also used to enable embedded SIM (E-SIM) on the phone. This attack is (virtually) more lethal to a person as the phone, or the SIM will not leave his hands or premises.
Details Required by Scammers to Do a SIM Swap Attack
Details required by re-issuance of a SIM depend on your country and the operator, but usually, they target the following information: The more information an attacker may have, the more chances he may succeed in his ill intent. With the mentioned information in the scammers’ hands, the attack could be so devastating (account takeover, identity theft, credit card fraud, etc.) that a victim may fail to restore his online identity fully.
Methods Used by Fraudsters to Choose Victims
An attacker may select victims by using the following method:
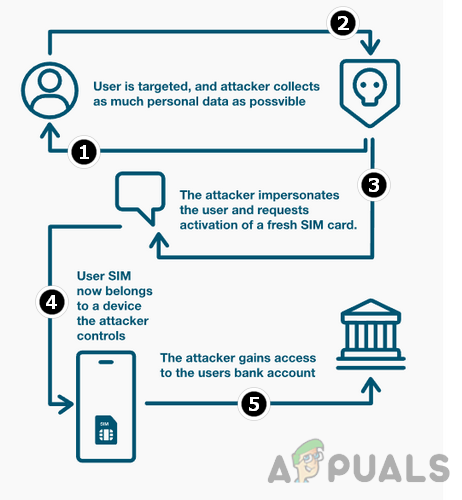
Steps in Performing the SIM Swap Attack
The general steps in a SIM swap attack can be listed as:
Usage of SIM Swap Attack by Fraudsters
The SIM swap attack is the basic step of fraud. Once a fraudster is in control of a victim’s phone number, he may use it for the following (but not limited to):
The severity of the Attack
To know the severity of the attack, let us quote an experience shared by a victim: “My entire digital life was destroyed in one hour after the SIM swap attack. Firstly, the scammer took over my Google account and then deleted it. Then, they logged into my Twitter account and started to broadcast racist/homophobic content. The worst was that they broke into my Apple ID account, and the scammers remotely erased the data of my MacBook, iPhone, and iPad. I do not have any backup of the data, so I have lost photos/videos of my daughter’s entire lifespan, and essential documents/emails were also lost.”
Warning Signs That You are Under a SIM Swap Attack
As you may have grasped the idea of how deadly a SIM swap attack can be, now here are some warning signs that you may notice when under attack:
Steps If You Are Attacked
If you are one of those unlucky ones who are suffering from the SIM swap attack, then you must take the actions listed below as the time is the key here:
Steps to Prevent the SIM Swap Attacks
There is a saying that prevention is better than cure, and there are some steps you may take to minimize the chances of SIM swap attacks. But the prevention is not the responsibility of a single entity, i.e., governments, telecom operators, financial institutes, and mobile phone subscribers. All must act in their respective domains to curb this scamming technique, as ignorance of any of these can lead to a successful SIM swap attack. A point to remember is that if a person is attacked once, then there are chances of more subsequent (probably automated) attacks if he does not take action to prevent attacks. Countries must bind the telecom operators to re-issue a SIM with proper verifications, and if there is a SIM swap attack, the country’s police must act to its maximum to capture the criminals involved. Otherwise, a successful SIM swap attack will be a moral booster for other criminals. Many countries are making laws and actions to counter this scam technique (FCC is already making rules in this regard). Telecom operators must make procedures to protect their customers from SIM swipe attacks. Operators must ensure that their employees do not fall for bribes offered by fraudsters. In this regard, T-Mobile already made some protocols to be followed by its employees before a SIM can be changed, like approval from two T-Mobile employees, which previously was tied to the approval of one manager; although it is not foolproof, it is a step in the right direction. Banks may use an API by the country’s regulator to check if there is a recent SIM swap, and if so, it should limit the client’s online access for a certain period or the client physically authorizes the swap. Also, using hardware authentication by a Bank should be a must to avoid any hacking of a client account. As a customer, you may adopt the following techniques to safeguard yourself from a SIM swap attack or repeated attacks (if already a victim). The basic purpose of these techniques is to break the vicious cycle that a victim may face if he becomes under attack by using the SIM swap method.
Check Your Country’s Regulations
The first step to counter SIM swap attacks should be to check your country’s regulations and see how your telecom operator is following the country’s regulations.
Check Your Operator’s Procedures to Issue a SIM
Try to properly understand your mobile carrier procedures for issuing a SIM, and if it offers any type of account management portal to manage your SIM or lock your phone number to a particular SIM, if so, then you may use it to safeguard yourself. If your operator is a little lousy in its procedures, you may get your number ported to a more secure operator (if possible). Even some operators provide a special code that you can dial from your phone to report any SIM swapping incident. Some operators may facilitate with a call-back feature. With the callback feature, whenever the mobile network operator is contacted for re-issuance of the SIM card of a probable victim, the operator may contact the probable victim on the phone number provided by the individual when settings up a call back feature and ensure that if he is legitimately requesting a SIM re-issue. If not, the operator will not issue a new SIM, and the attack will fail. So, if your mobile carrier has a call-back feature, use it to safeguard yourself from the SIM swap attack. Some operators have a time delay (around 72 hours) before a client’s SIM is swapped. Check if your carrier has any such facility. If so, activate it on your phone number so that you may have a time window before a scammer succeeds in his ill intentions.
Check Your Financial or Banking Procedures
Some banks (or financial institutes) are applying techniques to safeguard their customers against financial fraud by using SIM swap attacks. One such technique is to use the country’s regulator APIs to check if a client has recently swapped his SIM before performing transactions. If so, then the bank will limit the client’s transactions for a particular time or if the client physically verifies the SIM swap on a bank’s branch. The UK, Australia, and many African countries (like South Africa, Kenya, Mozambique, and Nigeria) have implemented the mentioned technique. So, check what is the safeguard by your bank against a SIM swap attack and follow any guidelines from the bank to avoid any SIM swap attacks.
Set a PIN or Password on Your SIM or Carrier’s Account Management Portal
As per the FTC recommendations, it is better for a mobile network subscriber to set up a PIN or password on his SIM. Also, to prevent changes to the subscriber’s phone number without the subscriber’s consent, a subscriber must lock his phone number in the carrier’s management portal (if available). If your carrier supports any of these, make sure to avail the feature to avoid any mishap in the future.
Avoid Sharing Personal Information
The cornerstone of a SIM swipe attack is the victim’s personal information required by mobile operators for re-issuance or porting a phone number to a new SIM. If a victim’s personal information is not available to an attacker, then the chances of attack by using the SIM swapping method are minimized but the attacker can still purchase a victim’s details from the black online market, given that the victim’s data was part of a data breach. So, to take advantage, ensure never to share your personal information with people on the phone or online (even if someone claims it is essential). Another technique used by fraudsters is to call a victim from a number looking like the mobile operator’s helpline number (or any government department like the health department) and try to gather the victim’s personal information. So, do not share your personal information over the phone, even with the persons claiming to be from the operator’s helpline or govt agencies.
Avoid Using Same Phone Number for Sensitive Accounts
A best practice that can be used is to use different phone numbers for different services (that will be a burden for some people) or another approach you can use is to use a single number for social media accounts and then another phone number for other services (like email, banks, etc.).
Stay Away from the Mentality that “I Am Safe”
When the fraudsters attack a number by using brute force method, they are shooting in the wild without knowing who the target is, and thinking that I am safe as I am not a high-profile individual may cost you your entire digital life (you may again read the Severity of the Attack section) and may cause other issues as well. There may be some people who may think that we have nothing to hide, but that is just a lame excuse because such people do not forget to close their house doors when leaving the house.
Use Landline Phone Numbers, eSIMs, or Virtual Phone Numbers
Whenever you are required to use a phone number, it is always better to use a landline number as it will protect you from a SIM swap attack. Also, if you are required to share your phone number online, go for a landline number. Moreover, in some countries, eSIMs may safeguard you against a SIM swap attack if the eSIM is only issued after the physical verification of the client on a company’s franchise. If you must use a mobile phone number and share it online, go for a virtual number like a Google Voice or Google Fi number.
Use a Different Type of Verification Method
Many services offer verification methods besides SMS like Google offers Google Authenticator to get codes when logging into Google or a hardware key offered by YubiKey. It will be better to use these alternatives to generate a login code (in place of SMS or call-based authorization), so that if you lose access to your account, you may still be able to log in using the authenticator app.
Use a Password Manager
Using common or similar passwords across websites is a great security hazard. It will be better to use a strong and unique password. If you are habitual of using common or similar passwords, you may switch to a password manager to avoid a catastrophe.
Stay Away from Suspicious Emails or Messages
If you are receiving emails or messages (even from close ones) that look suspicious, then you must not open those emails/messages or click any link in any emails/messages till you are 100% sure that the link is safe as scammers use suspicious emails or messages, or links in them to collect information about a probable victim and then carry on the SIM swap attack. Also, never download an attachment on your system/device until you are fully confident that the attachment is legitimate. Scammers mostly use these while keeping your interests (from your social media account) in their view, so do not fall for it.
Use Single Use Credit/Debit Cards
You may use online services (e.g., Privacy or Blur) to get single-use credit/debit cards or rechargeable credit/debit cards to avoid using your original single credit/debit cards online to avoid any damages that may occur if your original credit card info is stolen by scammers by using the SIM swap attack.
Use Bio-metric or Hardware Key Authorization
More and more services are shifting to bio-metric authorization. If your accounts or services support bio-metric authorization, it will be better to switch to those services to avoid SIM swaps or hacking attempts. If you are not comfortable using biometrics, you may adopt the hardware key authorization (like YubiKey).
Use Up-to-Date Security Tools on Your Devices
The web is not safe, and a person must use security tools (like antivirus, firewall, ad or pop-up blockers, etc.) to keep his data and information safe, especially from a phishing attack to gather the required information to carry on a SIM swap attack. Beware of those browser pop-ups or use an ad/pop-up blocker.
Never Share OTPs, 2FA Codes, or Take an Action That You Do Not Understand.
Scammers will try to use different techniques to lure the probable victims. They try to get OTP and 2FA codes from you to get your personal information. Also, if a person asks you to press a specific number key or perform an action on your phone, do not do that as you may be authorizing a SIM swap request as many operators require you to press a specific key (like 1 in India) to authorize a SIM swap operation. So that’s it, dear readers; we have tried our best to go through the topic and are hopeful that all of you will be safe from a SIM swap attack.
How to Protect Yourself from Zero-day AttacksHow to Enable Dual Sim on Single Sim Moto ZADATA SX8200 Pro Controller and NAND Swap – ExplainedProtecting yourself from Coronavirus (COVID-19) related Computer Scams